In the first part of this series, we took a factual and technical look at the history of the Internet. I explained how all of these wires and servers got here in the first place. Obviously, a firm did not just create and build the Internet around 1995! Now that we know how the Internet came to be, we can get into the really fun stuff—what the Internet looks like now!
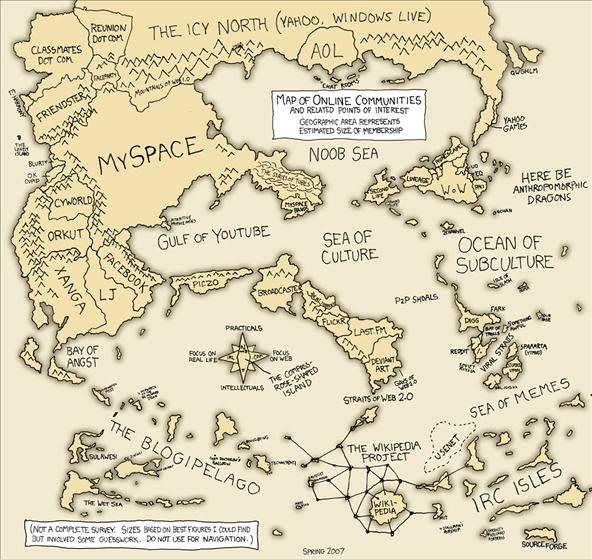
Well, that's not quite the network design I was talking about, but it does show what the Internet looked like back in 2007 before the great Facebook/MySpace War of '09. However, none of this would be possible if we didn't have an overarching scheme to connect the hardware in a way to allow all communication to happen relatively seamlessly.
Sending an email to your friend is simple enough. But it's a whole 'nother story to multiplex video, audio, and data all over the world at the speed of light—on demand. The global Internet is truly a feat of engineering, and soon you will understand why.
From a networking perspective, knowing this information and how it works will give you a better idea of what's happening under the hood, and it will allow you to work out issues and problems much more easily. What seems complex and daunting at first will be the springboard you use to get into the very gritty parts.
The View from the Top
To start out, let's look at the Internet like a giant 3D blob of interconnected networks and nodes. At the very bottom of this is you and me and every other normal home user. Little home networks are pretty much the ends of the Internet, as most do not serve anything out, instead they simply browse and take in data. This might be an unconventional view, but I think it serves us well here.
Now, when you turn on everything and try to visit a webpage, it doesn't look to my network for the resource. As we explained in our latest Hacker fundamentals article, sent requests check your home network and then ask the router for the correct path if it cannot be found locally. Now, we know what happens at the local level, but what happens from the wide area network level? How are these routes getting across the world?
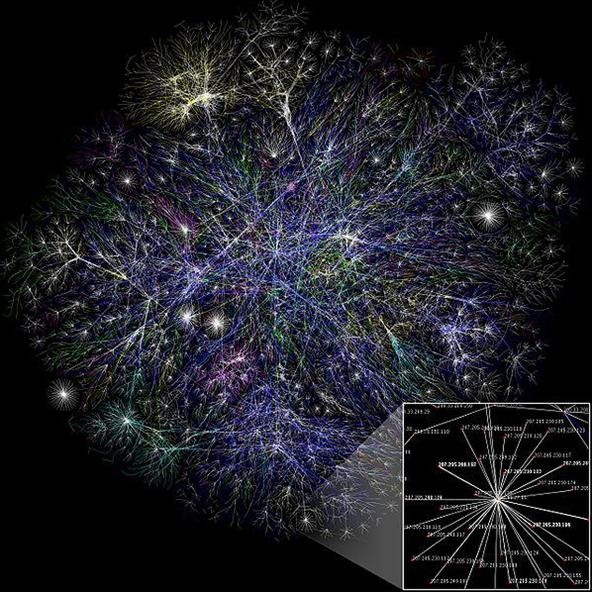
Turns out that your traffic is routed all across the world and actually not even as a whole, as it's broken into packets and those packets are sometimes sent on different routes to be reassembled upon receipt. But it doesn't just take random paths to the destination.
In the photo above, do you see where some of the lines converge and seem to "connect'" other webs? Those are high speed physical links between geographic areas that connect some of the Internet's largest subnetworks. Some of these are simply a benefit to speed and capacity, while others will cut off large areas of the Internet if severed. These links are called backbones.
Backbones: The Autobahn of the Internet
On the macro scale of the Internet, we have high speed dedicated routes that are loosely called backbones. These backbones refer to one of the principal data routes between large, strategically interconnected networks and core routers on the Internet. An backbone is a very high speed data transmission line that provides networking facilities to relatively small, but high speed Internet service providers all around the world.
Backbones are the largest data connections on the Internet. They require high speed bandwidth connections and high-performance servers/routers. Backbone networks are primarily owned by commercial, educational, government, and military entities because they provide a consistent way for Internet service providers to keep and maintain online information in a secure manner.
Some of the largest companies running different parts of the Internet backbone include UUNET, AT&T, and Sprint. Their routers are connected with high speed links and support different range options like T1, T3, OC1, OC3, or OC48. Also of note are the major underwater fiber optic cables ran under the world's oceans, as shown below.
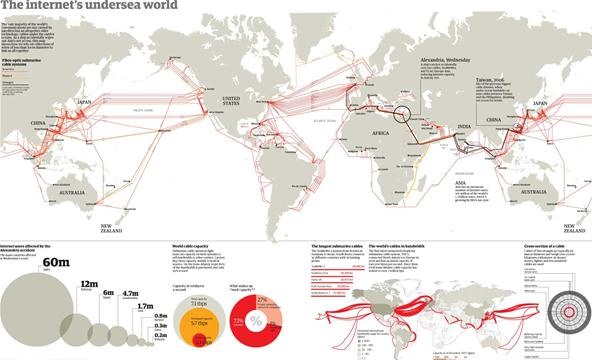
A few key features of an Internet backbone include:
- ISPs are either connected directly to their contingency backbones or to some larger ISP that is connected to its backbone.
- The smaller networks are interlinked to support backup that is required to keep the Internet services intact in case of failure. This is done through transit agreements and peering processes.
- The transit agreement is a monetary contract between several larger and smaller ISPs. It is initiated to share traffic loads or to handle data traffic in case of a partial failure of some networks. In peering, several ISPs also share features and traffic burden.
Core Routers
In a nutshell, a core router is a very large and very powerful router that handles huge amounts of traffic from various high speed lines and routes.
While the Internet has no center, some pieces of infrastructure are more important to smooth global functioning than others. The links running into Google's data centers are more important than your home cable modem. The core utilities of the Internet, such as Domain Name System root servers and core routers, are more critical still.
Because it's a network of networks, the Internet is resilient to damage. In networking terms, each independently operated network is known as an Autonomous System. Where two or more of these Autonomous Systems meet to exchange traffic, powerful core routers handle the data moving. It was this idea that led to the false rumor that Anonymous was going to attack these core routers to sever connections. Though the rumor was untrue, it is possible, as this white paper shows.
Basically, core routers do what your little AT&T 2Wire router does, but on a much larger scale.
From Backbones to ISPs
With these high speed links between geographical locations set, companies are able to branch capacity from them into smaller and smaller pipes. What will happen is a higher tier ISP will lease the bandwidth from above, then in turn re-lease the bandwidth out below it.
Once these links make it to the commercial ISPs, they branch out to your home network, through your personal router, and eventually to your computer.
In Closing
And that's it. From ARPAnet to Facebook. From Apple to Anonymous. This is the machine that churns in the background making the world turn. Hopefully some of the mystery behind it has been exposed and transformed into to a better understanding.
Do you have anything else to add to this? Leave me a comment below and check out our forum.
Articles like this and more! News from around the security industry—follow us on Twitter!
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























2 Comments
Actually a well written article .
Regards
Jacky
Very clear and precise!
Share Your Thoughts